Enterprise-Ready, Secure and Trusted SaaS Solution
Trust is the cornerstone of any successful partnership, which is why we provide every customer a reliable and secure SaaS offering. And since we believe trust also requires transparency, this page gives you an overview of how we protect your data and ensure compliance and system availability.
Availability
Your organization relies on access the availability of our software which thrives us to do everything in our power to ensure all systems are up and running at all times
Security & Compliance
We are compliant with GDPR and have several measures in place to ensure security.
Trust & Security Resources
We believe in transparency and therefore want to make it easy for you to find all relevant security and trust resources in one place.
Availability
You rely on us delivering the best and most reliable SaaS, which is why we build on modern technologies, best-in-class processes and transparency to ensure
the availability of our solution.
Building on Modern Technologies
An important part of ensuring availability is building a reliable foundation. For this reason, we decided to implement our software on the basis of a Microservices Architecture. Also, we make use of state-of-the-art technologies such as HighCharts and we aim to have a reasonable and maintainable tech stack, which can be viewed e.g. on stackshare.io.
Building on Modern Technologies
An important part of ensuring availability is building a reliable foundation. For this reason, we decided to implement our software on the basis of a Microservices Architecture. Also, we make use of state-of-the-art technologies such as HighCharts and we aim to have a reasonable and maintainable tech stack, which can be viewed e.g. on stackshare.io.
Microservices Architecture
Our software is divided into multiple component services (Microservices) to quickly and accurately repair or update bits and parts of the product without compromising the integrity of the application.
ReactJS
With our state-of-the-art ReactJs based UI (leveraging ReactJS maintaned by Facebook), we provide an excellent way to request exactly what you need, improving response times.
Transparent Tech Stack
We’re built ourselves on a modern technology stack and are happy to share it.
Transparent Perfomance Monitoring
We use different systems and mechanisms to monitor the performance as well as the availability and response-times of our solution. In case of incidents, we have a dedicated on-call-engineer who is available 24/7 to solve the incident.
Transparent Perfomance Monitoring
We use different systems and mechanisms to monitor the performance as well as the availability and response-times of our solution. In case of incidents, we have a dedicated on-call-engineer who is available 24/7 to solve the incident.
Availability and Response-Time
We make the availability and response-times of our software available to our customers upon request, these are measured continously with pingdom.com.
Application Performance
Using solutions like Pingdom and New Relic, we constantly monitor Decision Focus performance to stay aware of issues.
Dedicated 24/7 On-call-Engineer Setup
Our on-call service with IBM Cloud is always available to fix critical issues to ensure a speedy resolution.
Built for Scale
Decision Focus is built for scale. We allow customers to manage users directly from a single, central directory using either the native indentity management setup, LinkedIn or any 3rd party SSO Identity Provider.
Built for Scale
Decision Focus is built for scale. We allow customers to manage users directly from a single, central directory using either the native indentity management setup, LinkedIn or any 3rd party SSO Identity Provider.
Built-in Identity Managment
Decision Focus comes with a built-in Identity Management and a comprehensive roles and rights model to ensure compliance.
Integrate with SSO Identity Providers
Have a 3rd party SSO Identity Provider in place? Not a problem—Decision Focus can easily integrate with all SAML 2.0 compliant providers.
Scalable Hosting
Built from the ground up on IBM Cloud, secures worldwide delivery and guarantees world-class availability.
Security & Compliance
Data Security
We ensure data protection and are committed to keeping customer information safe and secure. IBM data centers are ISO 27001 and SOC2 certified.
Decision Focus has robust password policies in place and ensure data encryption. And by following the Principle of Least Privilege (PoLP) we ensure only necessary privileges are given.
We are ISO 27001 certified
Decision Focus is ISO 27001 certified for Information Security Management System
Data Encryption
Data is encrypted in transit using TLS1.2 protocol with a strong ECDHE-RSA suite.
Data is also encrypted at rest.
Robust Password Policies
To ensure data security on an employee level, passwords are hashed using a strong bcrypt algorithm. Strong password configurations are enforced in line with global best practices.
Principle of Least Privilege (PoLP)
We follow the Principle of Least Privilege (PoLP) and employees are given only privileges that are necessary for performing their duties.
IBM Cloud and SOC2
The Decision Focus hosting setup at IBM is SOC2 certified and complies with a range of other security standards.

Security Baked-in
We believe that security must be part of the foundation, so we rely on secure hosting partners and regular penetration testing. In addition, on every customer setup, we have a dedicated security page, delevering daily basis of vulnerability scans.
Security Baked-in
We believe that security must be part of the foundation, so we rely on secure hosting partners and regular penetration testing. In addition, on every customer setup, we have a dedicated security page, delevering daily basis of vulnerability scans.
DevOps
We deliver our entire solution on DevOps tooling and principles. This enables us to rectify any important security issues swiftly, across all customers, all geographies and with no customer intervention.
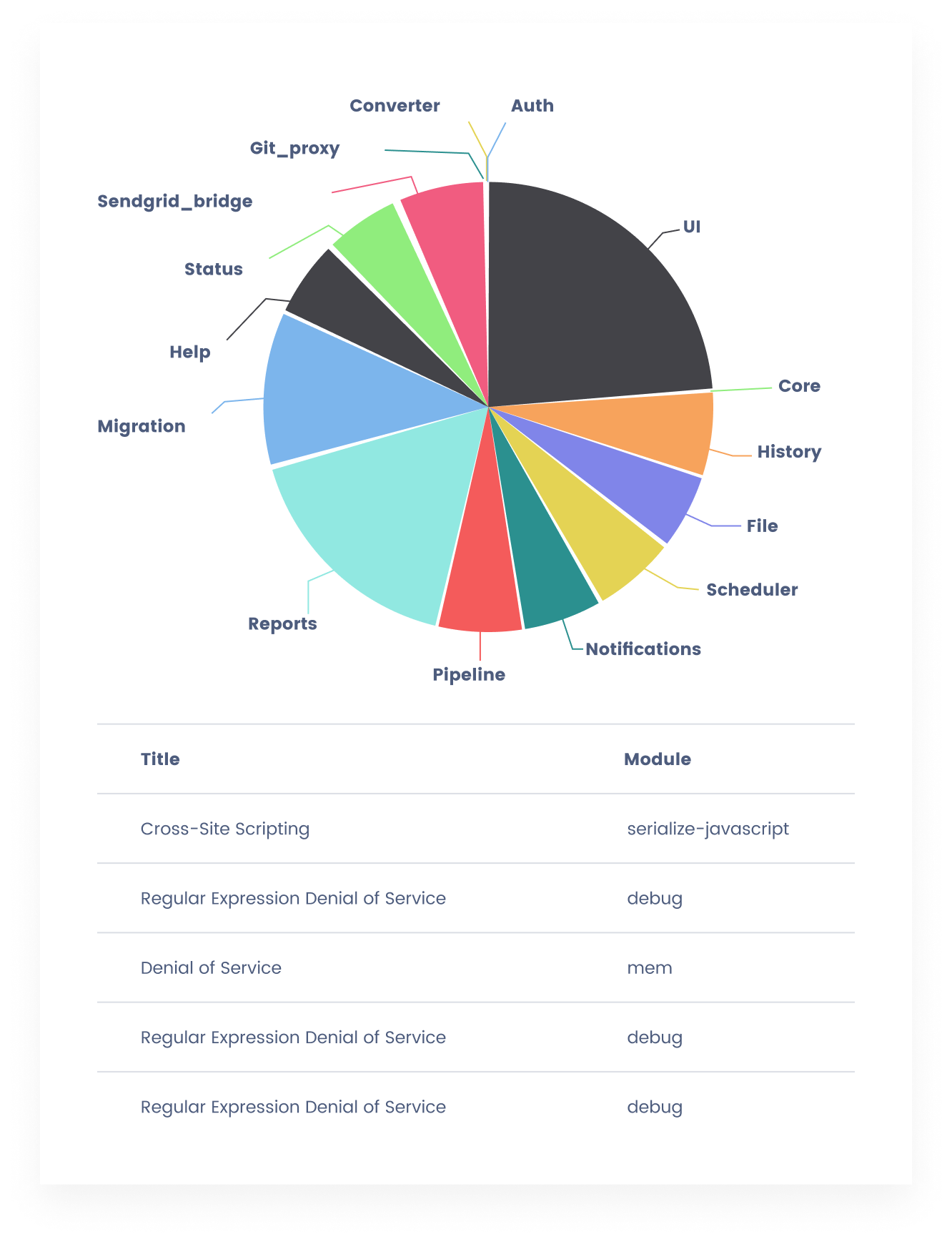
Regular Penetration Testing
Penetration tests are performed on Decision Focus by external experts and cover all vulnerability aspects of the application. Decision Focus is using the world’s largest software registry to scan for known vulnerabilities.
Automated Self-Audit
Penetration tests are performed on Decision Focus by external experts and cover all vulnerability aspects of the application. Decision Focus is using the world’s largest software registry to scan for known vulnerabilities.
Trust & Security Resources
Find links to resources covering relevant information on Decision Focus Availability, Modern Architecture, Data Security and Compliance
Any questions?
The Decision Focus team are here to answer your questions.


